- Home
- Case Study
- Case Study – Managed SOC Services for a Large Conglomerate
Managed SOC Services for a Large Conglomerate – Focus on Microsoft 365 (M365) Security
Client Overview
Client: Large Conglomerate
Industry: Corporate (Various Sectors)
Project: SOC Services and Microsoft 365 (M365) Security Monitoring
This large conglomerate required a robust managed security solution to monitor their Microsoft 365 (M365) environment, with a focus on preventing internal threats, data leakage, and account compromises.
Client Challenges
The client moved to M365 but lacked adequate security monitoring, leading to concerns over potential internal threats and data leakage from compromised M365 accounts. The company required a comprehensive managed security solution that could detect and respond to malicious activities in real-time. Without sufficient monitoring, sensitive company data and resources were vulnerable to both internal and external threats.
Our Solution
SOC Services with AI Detection:
We implemented SOC services to monitor the M365 platform, including authentication logs and file activity monitoring, utilizing AI-driven threat detection to identify malicious behaviors in real-time.
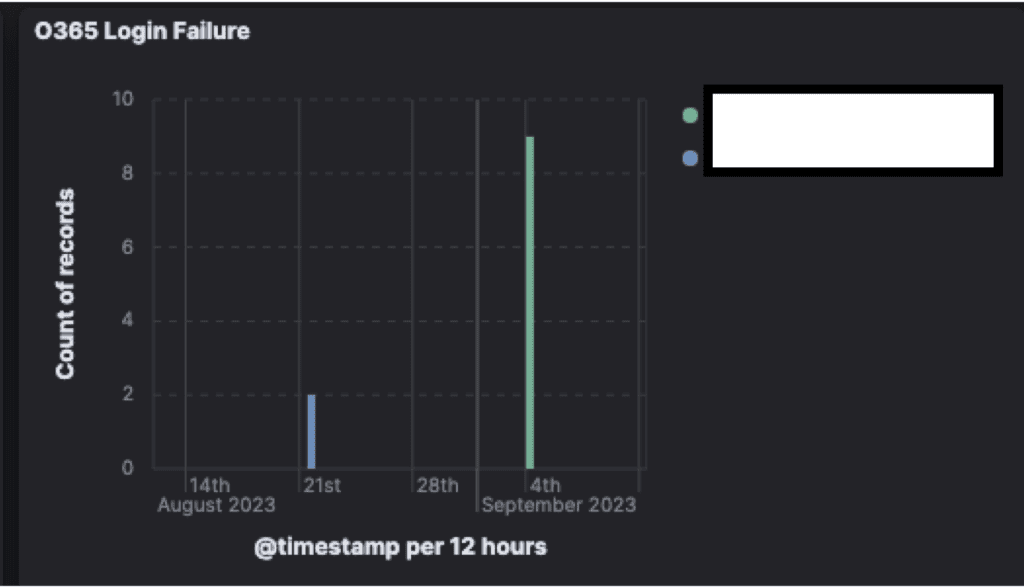
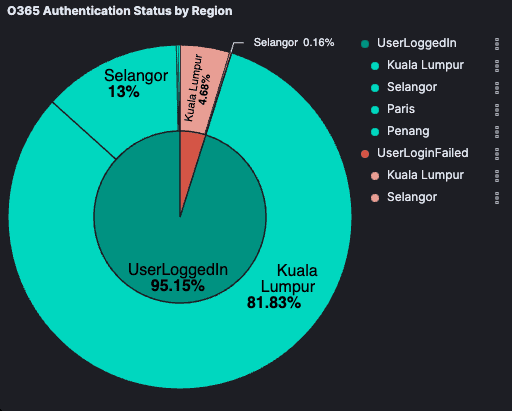
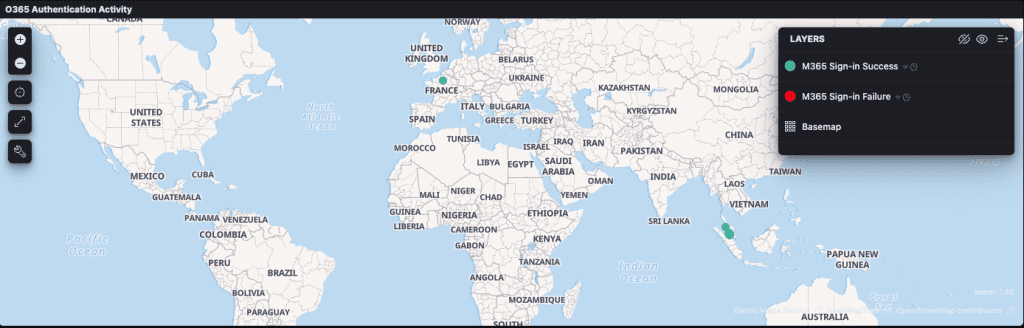
Proactive Threat Hunting
Our security team conducted proactive monitoring, detecting compromised M365 accounts and identifying internal threats such as data leakage from employees. This enabled us to act before any significant breaches occurred.
Key Insights: O365 Monitoring for Data Protection
Effective O365 file activity monitoring is crucial to detect and prevent data leaks and other internal threats. Here’s how Simply Data’s solution helped address key areas of concern:
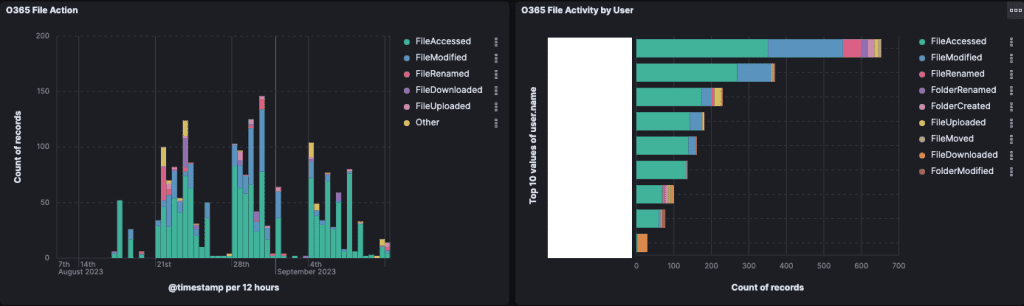
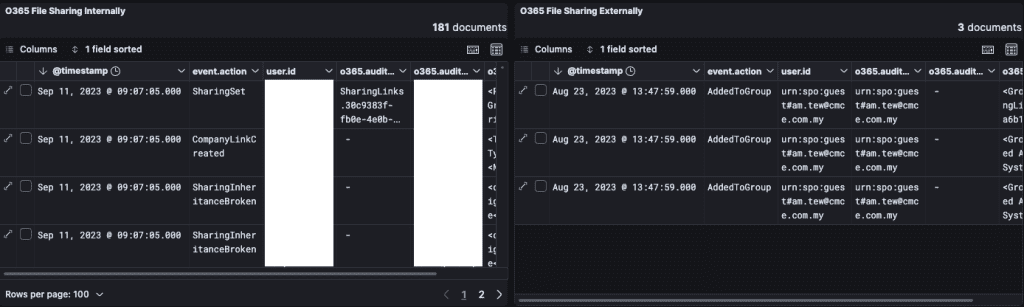
Simply Data’s O365 monitoring tracks every file-related action, such as file access, file modification, and file renaming, within the M365 environment. The monitoring system captures important timestamps and user actions, helping organizations to track who is accessing or altering files at any given time. This visibility is key in preventing unauthorized access and maintaining data integrity.
Internal and External File Sharing
Our monitoring solution differentiates between internal and external file sharing to ensure no sensitive data is inadvertently or maliciously shared outside the organization. Here’s how we handle both:
Internal File Sharing:
The system tracks when files are shared within the organization, such as sharing between departments or colleagues. It also identifies any unusual file activity patterns, helping organizations detect if sensitive data is being shared improperly.
External File Sharing:
When files are shared with external parties (e.g., clients, contractors), the system ensures that no confidential documents are being exposed without proper authorization.
Data Leakage Identification
The monitoring system identifies potential data leakage when an employee shares sensitive documents or exports files before resigning or leaving the organization. We track specific actions like ‘AddedToGroup’ to indicate that files are being transferred or shared without proper authorization, ensuring that your organization’s data protection policies are always enforced.
Compromised M365 Accounts
Simply Data’s O365 monitoring solution also helps uncover compromised M365 accounts. If a malicious actor gains unauthorized access to an employee’s account, our system can detect suspicious behavior, such as unauthorized file access or unusual login locations, through file-sharing logs and authentication details.
Benefits of Our Solution
Our solution delivers several critical benefits to our clients, ensuring they remain secure against both internal and external threats:
- Uncover Data Leakage via Internal Threats: Detect actions that could lead to sensitive data being accessed or shared improperly within the organization.
- Monitor Compromised M365 Accounts: Prevent data theft or breaches by continuously monitoring file-sharing activities and detecting suspicious actions linked to compromised accounts.
- Ensure Continuous Security Compliance: Maintain high levels of data security by monitoring authentication logs, file activities, and detecting any unauthorized access.