- Home
- Case Study
- Case Study – Security Operations Center (SOC) for a Large Government
Security Operations Center (SOC) for a Large Government-Linked Corporation (GLC)
Client Overview
Client: Large Government-Linked Corporation (GLC)
Industry: Public Sector (Government Agency)
Project: Security Operations Center (SOC) Managed Services
This Government-Linked Corporation is a national organization responsible for providing public services. They needed an effective, real-time security monitoring solution to safeguard sensitive national workforce data, which could be severely impacted by any breach.
Client Challenges
The client faced major challenges in securing their infrastructure:
1. Lack of Proactive Monitoring: With limited security monitoring in place, the client was unable to detect hidden threats that could compromise the sensitive data they manage.
2. Impact of Breach: Any breach in their server infrastructure could have devastating effects on the nation’s workforce data, requiring immediate attention to prevent any potential risks.
Our Solution
Simply Data Sdn Bhd implemented an integrated, 24/7 Security Operations Center (SOC) solution to address the client’s security needs. Here’s how we helped:

24/7 SOC Services
We provided round-the-clock SOC services, ensuring continuous monitoring of the client’s infrastructure. This helped us quickly identify and respond to threats, minimizing any potential risk to sensitive national data.

Proactive Threat Hunting
To uncover threats that were not detected by traditional security layers, our team carried out proactive threat hunting. We actively searched for hidden threats in the client’s network, identifying potential risks and taking action before they could escalate.

Incident Reporting & Response
Whenever a suspicious activity or potential breach was detected, we generated detailed incident reports and immediately responded to contain the threat. Our incident response team acted quickly to neutralize risks and provided the client with recovery steps.
The Incident – As Below Screenshot
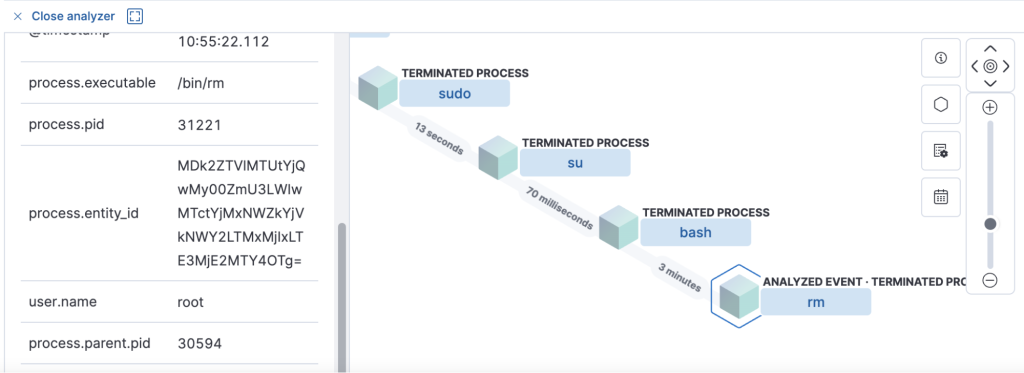
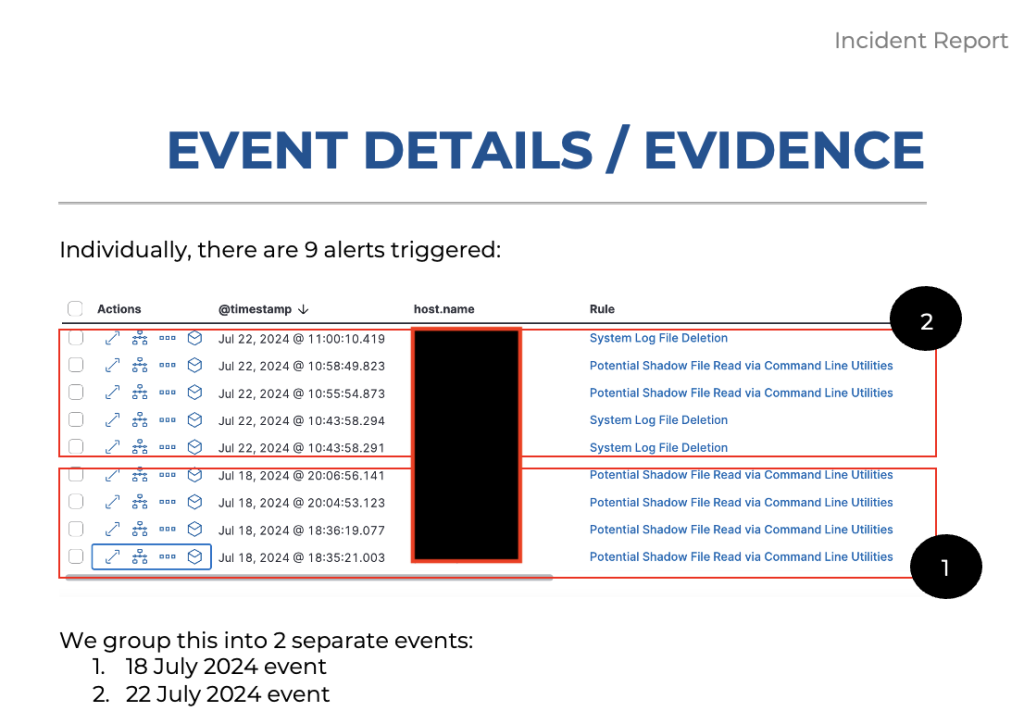
- Attacker used valid admin credentials to login, read sensitive files, and delete its login traces.
- Incident report created, threat contained, and SOC advised recovery / remediation steps.
The Results
Uncovered Hidden Threats: Our proactive threat hunting methods helped identify and mitigate hidden threats that had previously bypassed four layers of security.
Minimized Risk: By implementing 24/7 SOC services, the client was able to reduce the risk of breaches and data loss, ensuring continuous operation of their essential services.
Improved Data Security: With ongoing monitoring and quick incident response, sensitive workforce data was effectively safeguarded from potential threats.